
Build a Stronger Security Posture with Cyber Asset Intelligence
The attack surface is growing, fast. Lansweeper empowers security teams with total visibility into every connected asset —IT, OT, IoT, and cloud— so they can detect threats early, respond quickly, and stay compliant. It’s your foundation for a stronger, more resilient security posture.
-

Finding Risk
Uncover hidden vulnerabilities across your network with Lansweeper’s comprehensive asset visibility.
-

Prioritizing Risk
Tailor risk management to your needs with customizable prioritization. Address the most critical threats first for maximum protection.
-

Mitigating Risk
Streamline risk reduction with seamless integration into your existing tools. Mitigate vulnerabilities swiftly and effectively.
-

Tracking Risk
Stay on top of vulnerability resolution and keep your security posture strong with security-focused audit reports.

Unknown Assets, Unknown Risks
Blind spots are security’s biggest liability. Shadow IT, unmanaged devices, and misconfigurations often go unnoticed—creating exploitable gaps. Without a centralized inventory of assets, security teams struggle to detect vulnerabilities, investigate incidents, and enforce controls, increasing risk and slowing down every layer of defense.

Discover Your Entire Attack Surface
Automatically discover all connected devices —IT, OT, IoT, and cloud— across hybrid environments. Lansweeper ensures no device goes unseen, enabling continuous monitoring and proactive protection of your complete digital estate.
Reduce Cyber Risk with Smarter Attack Surface Management
Every new device expands your attack surface. Lansweeper supports CAASM by continuously identifying vulnerable assets—before attackers do. With comprehensive, real-time data on every asset, you can shrink your exposure, reduce blind spots, and proactively defend your environment.
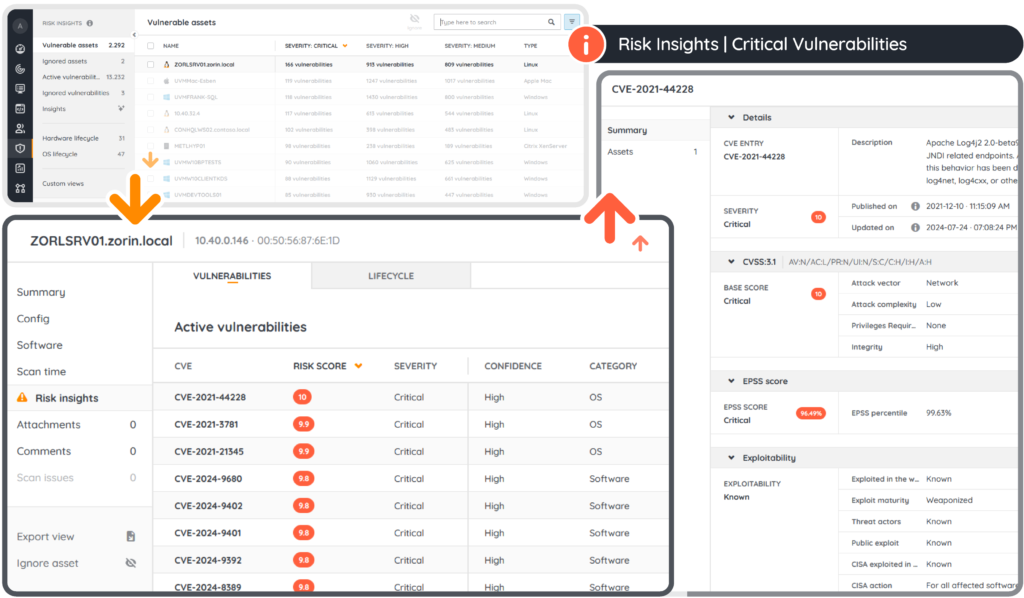
Prioritize Risks That Matter Most
Lansweeper’s customizable Risk Insights help you focus on what matters most. Instead of reacting to every vulnerability, you prioritize threats based on real-world exploitability, asset criticality, and organizational context—reducing noise and improving response time.
Empowering Every Role in Security
One platform. Value for every security persona. From CISOs to frontline analysts, Lansweeper delivers the visibility and context needed to reduce risk and respond with confidence.
-

CISO / Security Leader
View your full risk landscape, align strategy to data, and prove security posture to stakeholders.
-

Security Analyst
Investigate and respond faster using accurate asset context across incidents, alerts, and events.
-

Vulnerability Manager
Continuously discover and prioritize vulnerabilities across all assets for focused remediation.
-

Compliance Officer
Ensure ongoing alignment with regulatory frameworks through accurate, automated asset tracking.
With Lansweeper, we can gather data very quickly and know how to focus our efforts. From an incident response perspective, it helps us reduce the time it takes to respond to incidents so we can contain them faster. Risk is reduced because we are faster and more effective at resolving issues — and that’s invaluable.

Respond to Incidents Faster

Contain Threats at the Source
Lansweeper maps device relationships and communication flows to support network segmentation and micro-isolation. This enables stronger access controls and reduces lateral movement—minimizing the damage of potential breaches.
Simplifying Audits and Regulatory Compliance
Security regulations demand accurate inventories and audit trails. Lansweeper automatically collects and maintains audit-ready records on hardware, software, configurations, and controls—so you’re always prepared for NIST, ISO 27001, DORA, and other frameworks.


Your Cybersecurity Stack, Supercharged
Lansweeper integrates seamlessly with your favourite security platforms, fueling them with always-accurate asset intelligence. Take your security workflows to the next level with comprehensive, continuously updated asset data.
- Integrations
Connect with ServiceNow, Atlassian, HaloITSM, Axonius, and more. - API
Leverage powerful developer tools to build custom integrations.
- Workflows
Streamline IT operations with automated workflows.
Ready to get started?
You’ll be up and running in no time.
Explore all our features, free for 14 days.






















